-
Financial administration & outsourcing
Entrepreneurs who outsource financial administration reduce the number of administrative tasks and consequently have more time and space to focus on growth.
-
Financial insight
We help you turn financial data into valuable insights that support you in making well-founded decisions. In-depth analyses of your financial situation will help give you a better idea of where you stand and where the opportunities for growth lie, both in the short and long term.
-
Financial compliance
We make sure your company complies with financial legislation and regulations, with correct financial statements, tax reports and other obligations. From our global network, we support you in managing local and international tax risks.
-
Impact House by Grant Thornton
Building sustainability and social impact. That sounds good. But how do you go about it in the complex world of stakeholders, regulations and frameworks and changing demands from clients and society? How do you deal with important issues such as climate change and biodiversity loss?
-
Business risk services
Minimize risk, maximize predictability, and execution Good insights help you look further ahead and adapt faster. Whether you require outsourced or co-procured internal audit services and expertise to address a specific technology, cyber or regulatory challenge, we provide a turnkey and reliable solution.
-
Cyber risk services
What should I be doing first if my data has been kidnapped? Have I taken the right precautions for protecting my data or am I putting too much effort into just one of the risks? And how do I quickly detect intruders on my network? Good questions! We help you to answer these questions.
-
Deal advisory
What will the net proceeds be after the sale? How do I optimise the selling price of my business or the price of one of my business activities?
-
Forensic & integrity services
Do you require a fact finding investigation to help assess irregularities? Is it necessary to ascertain facts for litigation purposes?
-
Valuations
Independent and objective valuations tailored for mergers, acquisitions, and legal matters.
-
Auditing of annual accounts
You are answerable to others, such as shareholders and other stakeholders, with regard to your financial affairs. Financial information must therefore be reliable. What is more, you want to know how far you are progressing towards achieving your goals and what risks may apply.
-
IFRS services
Financial reporting in accordance with IFRS is a complex matter. Nowadays, an increasing number of international companies are becoming aware of the rules. But how do you apply them in practice?
-
ISAE & SOC Reporting
Our ISAE & SOC Reporting services provide independent and objective reports on the design, implementation and operational effectiveness of controls at service organizations.
-
International corporate tax
The Netherlands’ tax regime is highly dynamic. Rules and the administrative courts raise new challenges in fiscal considerations on a nearly daily basis, both nationally and internationally.
-
VAT advice
VAT is an exceptionally thorny issue, especially in major national and international activities. Filing cross-border returns, registering or making payments requires specialised knowledge. It is crucial to keep that knowledge up-to-date in order to respond to the dynamics of national and international legislation and regulation.
-
Customs
Importing/exporting goods to or from the European Union involves navigating complicated customs formalities. Failure to comply with these requirements usually results in delays. In addition, an excessively high rate of taxation or customs valuation for imports can cost you money.
-
Innovation & grants
Anyone who runs their own business sets themselves apart from the rest. Anyone who dares stick their neck out distinguishes themselves even more. That can be rather lucrative.
-
Tax technology
Driven by tax technology, we help you with your (most important) tax risks. Identify and manage your risks and become in control!
-
Transfer pricing
The increased attention for transfer pricing places greater demands on the internal organisation and on reporting.
-
Sustainable tax
In this rapidly changing world, it is increasingly important to consider environmental impact (in accordance with ESG), instead of limiting considerations to financial incentives. Multinational companies should review and potentially reconsider their tax strategy due to the constantly evolving social standards
-
Pillar Two
On 1 January 2024 the European Union will introduce a new tax law named “Pillar Two”. These new regulations will be applicable to groups with a turnover of more than EUR 750 million.
-
Cryptocurrency and digital assets
In the past decade, the utilization of blockchain and its adoption of a distributed ledger have proven their capacity to revolutionize the financial sector, inspiring numerous initiatives from businesses and entrepreneurs.
-
Streamlined Global Compliance
Large corporations with a presence in multiple jurisdictions face a number of compliance challenges. Not least of these are the varied and complex reporting and compliance requirements imposed by different countries. To overcome these challenges, Grant Thornton provides a solution to streamline the global compliance process by centralizing the delivery approach.
-
Private wealth services
Our Private Wealth specialists offer strategic and practical solutions. From tax advice to estate planning and financial scenarios, we make sure you make the right choices today, for tomorrow.
-
Corporate Law
From the general terms and conditions to the legal strategy, these matters need to be watertight. This provides assurance, and therefore peace of mind and room for growth. We will be pro-active and pragmatic in thinking along with you. We always like to look ahead and go the extra mile.
-
Employment Law
What obligations do you have with an employee on sick leave? How do you go about a reorganisation? As an entrepreneur, you want clear answers and practical solutions to your employment law questions. At Grant Thornton, we are there for you with clear advice, from contracts and terms of employment to complex matters such as dismissal or reorganisation.
-
Sustainable legal
At Grant Thornton, we help companies integrate sustainability into their business operations, with sustainable legal at the heart of our approach. We advise on ESG (Environmental, Social, Governance) legislation, and help draft sustainable contracts, implement HR policies, and carry out ESG due diligence in M&A transactions (Mergers and Acquisitions).
-
Pension advisory services
Are you, as business owner or employer, well prepared in terms of pension and other future facilities?
-
Global mobility services
How can you build and evolve a smart global mobility strategy, with policies and processes addressing the complex challenges of managing an international workforce?
-
Maritime sector
How can you continue to be a global leader? The Netherlands depends on innovation. It is our high-quality knowledge which leads the maritime sector to be of world class.
What should I be doing first if my data has been kidnapped? Have I taken the right precautions for protecting my data or am I putting too much effort into just one of the risks? And how do I quickly detect intruders on my network? Good questions! We help you to answer these questions.
Grant Thornton has identified five essential risk areas for a good assessment. We check:
- our employees’ security awareness;
- your internal network;
- your WiFi network;
- the ‘endpoint devices’, such as your laptops and mobile phones;
- and the physical infrastructure of your organisation.
Together we chart the risks and test your organisation’s security in the chosen risk areas. Our cyber security assessment is offered in our various services. Furthermore, we can also ensure that your organisation is able to react quickly and effectively if a cyber attack takes place.
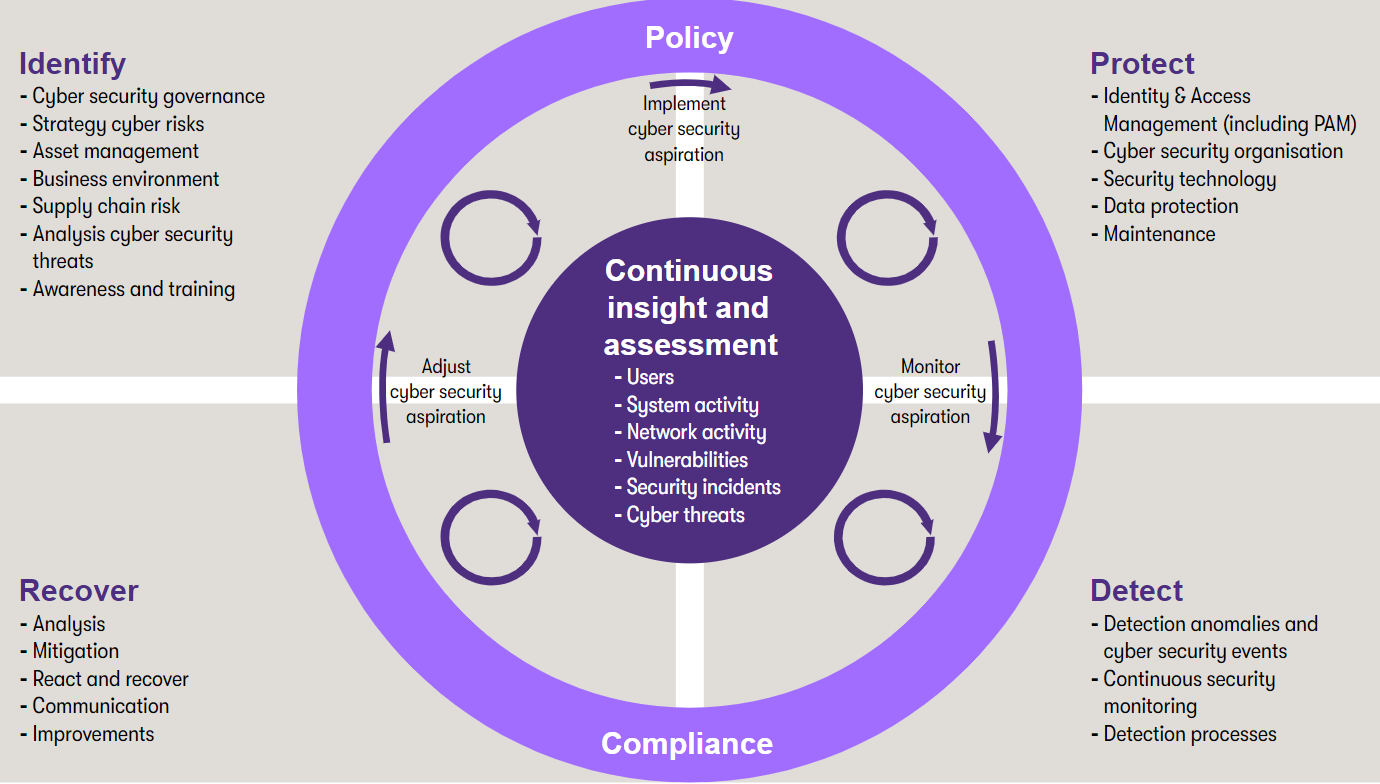
These are our various cyber risk services
Cyber strategy & compliance offers you a pragmatic insight into your data-dependence and the weak points in your information security. A few practical actions and measures can protect your organisation in no time. Plus, you’ll fully meet all the legal requirements. And if it does go wrong: you’ll even have a script ready for when a cyber attack happens.
Have I taken the right precautions to secure my data? To investigate that, our Cyber protection & incident response team will scour through your organisation to find all the security risks. We use our ethical hackers, for example. They conduct a penetration test on your network, so that you know where the weak spots are. Then, together, we ensure that your organisation keeps these risks under control, including a disaster plan and full compliance.
How do I quickly detect intruders on my network? Using Managed cyber is the short answer! We understand that cyber security is not your core business. That is why we offer it as a service: your network will receive regular monitoring, throughout the year.

